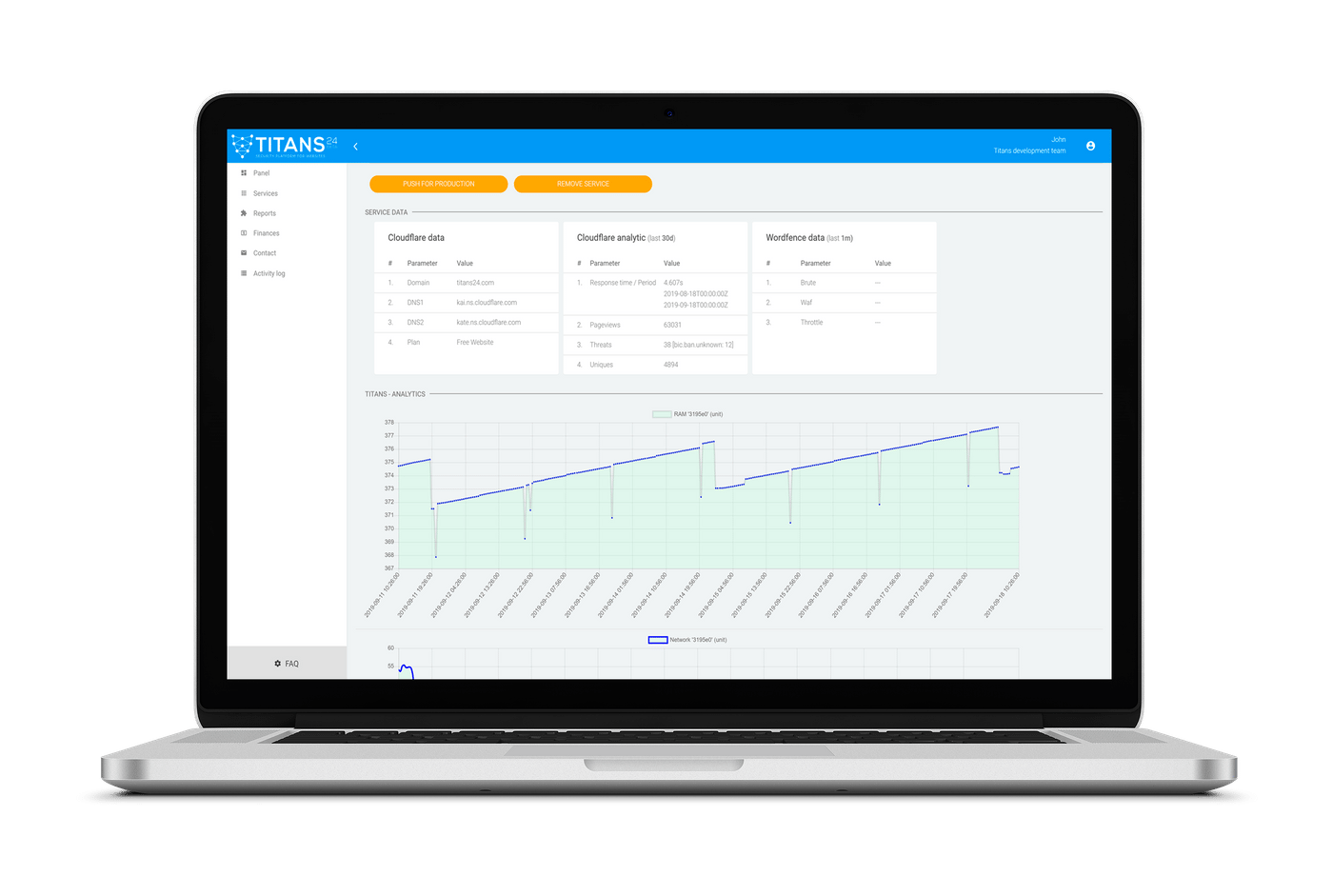
Titans24 — Secure Application as a Service. A security platform for your company.
We’re a team of cybersecurity professionals and legal experts behind the technology that your company uses to:

Hacking, errors, breaches, DDoS
Our infrastructure is designed to save your employees time while allowing them comfortable management of your company’s applications.

Digital data security
Protection of your data in CMS systems, within e‑commerce projects, and in databases.

Fast website access under high
availability
100% access to your web page, Web service or e‑commerce.
Technological advantage
Titans24 employ the latest tech for digital access and storage that were adopted by the market. Regardless of what you know about IT — this stuff is bigger.

High availability
Our infrastructure is a swarm of nodes scattered between TIER 3/3+ ATMAN, OVH, and GCE servers with full redundancy and real-time communications. This guarantees SLA as in: Total SLA = 99,99% ATMAN * 99,99% OVH* 99,99% GCE* n. Here, n is the number of nodes used by Titans24 to maintain a given service or application and n >=3.

Automatic anti-malfunction switch
Your application takes at least one container. Each container retains a visual matrix with its control sum used to verify the source code. All containers have a Fingerprint such as this which ensures validity in truth/false tests.
Containerization of applications
Your service operates in a number of parallel copies which is adequate to number of active T24 nodes. In case of any problems with a node, the system will automatically redirect the application to a functional address. In case of any malfunctions, you’ll be always able to restore the container’s previous state.
Scalability of assets
Our infrastructure is a swarm of nodes scattered between TIER 3/3+ ATMAN, OVH, and GCE servers with full redundancy and real-time communications that are located in Poland and in other EU countries. This guarantees the continuity of online access.
Support for legal advisers
With legal offices specialising in IT law as our partners, we are able to offer sure legal counseling in terms of RODO — on top of delivering solid technological backup.

GDPR and RODO compliance
We’ve been following RODO regulations since May 2018 with all the precautions covered. Titans24 will ensure that the right to be forgotten is convenient to handle for your service.

Crisis management
We oversee the production and integration of safety procedures for verified and potential threats. Procedures themselves come from lawyers specialised in cyberdefense on the grounds of an audit. Our goal is to provide „Full damage control”.

Domain and application health monitoring
Low domain reputation is often the result of years of mismanagement. But you don’t have to worry about MX records or compatibility anymore. Our admins will provide the right setup for it — we’ll work on it like it’s ours.

Accessibility
At all times, you can access the dashboard for your application to see its structure and availability. Depending on your needs, you may focus solely on the growth of the application after the migration without worry about the infrastructure.
Stable and fast infrastructure
Access to your applications is monitored on every level — our years of software development practice resulted in best achievable cybersecurity measurements.

Active security
We’re offering 10 interdependent security layers for each application, including: swarm intelligence, multilevel firewall, risk mitigation, brute force protection, country blocking, manual blocking, IP scanner, and a malware scanner, among many others.

Access control
We follow strict procedures that regulate access control. We’re providing you with access management on administrative and user levels. Entry to core features is diversified while still under access level privileges.

Process automation
We’re speeding up all that’s repetitive — establishing development environment, backup recovery, tests, monitoring, or data migration. Start saving your time by leveraging Machine Learning and our experience.
SSL
All subscription plans grant you a basic SSL certificate. It’s important to have it, as it encrypts the connection with the service. SSL directly increases your domain’s security and the trust it receives from users and Google.

